
Overview of ICS-SCADA
- A modern Supervisory Control and Data Acquisition (SCADA) system is a centralized computer application that monitors and controls a plant or equipment at the supervisory level.
- There are many types of SCADA systems, and they can be used to manage any type of equipment to automate where manual monitoring and control by human staff just isn't feasible.
- Industrial system (ICS) together with its parts (SCADA, PLCs, and RTUs, etc.) square measure usually employed in industries
- Numerous companies in the industries use these systems to automate complex industrial processes, detect and correct problems, and measure trends over time
- These systems provide companies monitoring and control applications by collecting and analyzing real-time data
- The 4 functions performed by a SCADA network are:
- Data acquisition
- Networked data communication
- Data presentation
- Control
Recent Event Related to SCADA
- The Maharashtra cyber department suspects that a malware attack could be responsible for Mumbai's power outage last month.
- Sources in the Maharashtra cyber department have revealed that in their initial investigation they have traced the infusion of malware at the Padgha-based state load dispatch center.
- The load dispatch center works on an automated system where data is monitored and could have been attacked. Maharashtra Power Minister Nitin Raut had earlier said the department suspected sabotage behind the power failure leading to the outage.
- The suspicious logins have been traced to Singapore and other South Asian countries.
- These kinds of incidents are very dangerous, power grids are critical infrastructure and a cyber attack could impact hospitals, research institutes, and other critical areas.
Reason for the Rise
- Increased number of entry points and paths
- Increased connectivity
- An increased amount of collection and transmission of customer information
- Increased development and use of the new system and network technologies
Problems of Industrial IT/OT Systems
- Maintenance personnel or subcontractors can have excessive access to the SCADA computers or PLC.
- Electricians or mechanics, who have physical access to the industrial computers but lack proper authorization, can copy or modify the industrial software
- Industrial Ethernet networks can have An unauthorized person access the network and copy or change the PLC program via Profibus, Modbus, CAN, Profinet, and other buses, which are normally used for remote IO and slave devices but can also be used for PLC programming
- Industrial Ethernet networks can have unauthorized connections (temporary, debug, etc.) to other enterprise or office networks. WiFi/GPRS/3G modems or routers can have an unauthorized connection to the industrial switches. Industry 4.0 / Industrial Internet of Things (IIoT) methods require an Internet connection, which dramatically increases the security risks.
- The migration of PLC to PC-based automation (SoftPLC, etc.) increases security risks. Common vulnerabilities of operating systems will apply in addition to controller-specific vulnerabilities
- Relying only on network segmentation and ignoring other security measures (such as access control on all levels, configuration management, security event monitoring, update of software and operating systems, antiviruses, firewalls, user security rules, password policies, etc.) results in an accumulation of security problems over time.
Whom Does SCADA Audit Applies To?
SCADA systems are the backbone of many modern industries, including:
- Energy
- Food and beverage
- Manufacturing
- Oil and gas
- Power
- Recycling
- Transportation
- Water and wastewater and many more.
What are the Frameworks & Standards Used?
- ISO/IEC 27001, VDA ISA, ENX TISAX®
- ISA99, ISA/IEC 62443
- North American Electric Reliability Corporation (NERC) Reliability and Security Guidelines
- NIST SP 800-82 Guide to Industrial Control Systems (ICS) Security, NIST Framework for Improving Critical Infrastructure Cybersecurity
- DHS guidelines for critical infrastructure protection and the Critical Infrastructure Protection framework
- Specific vendors. For example, we work with Siemens PLCs using Step7 and TIA Portal, with Schneider Electric equipment using Concept, UnityPro, and SoMachine, with Mitsubishi using GX Works, with Omron using CXOne, with Carel using 1tool, and with Wago using CoDeSys.
Key Cyber Security Maturity Model Certification Project Deliverables
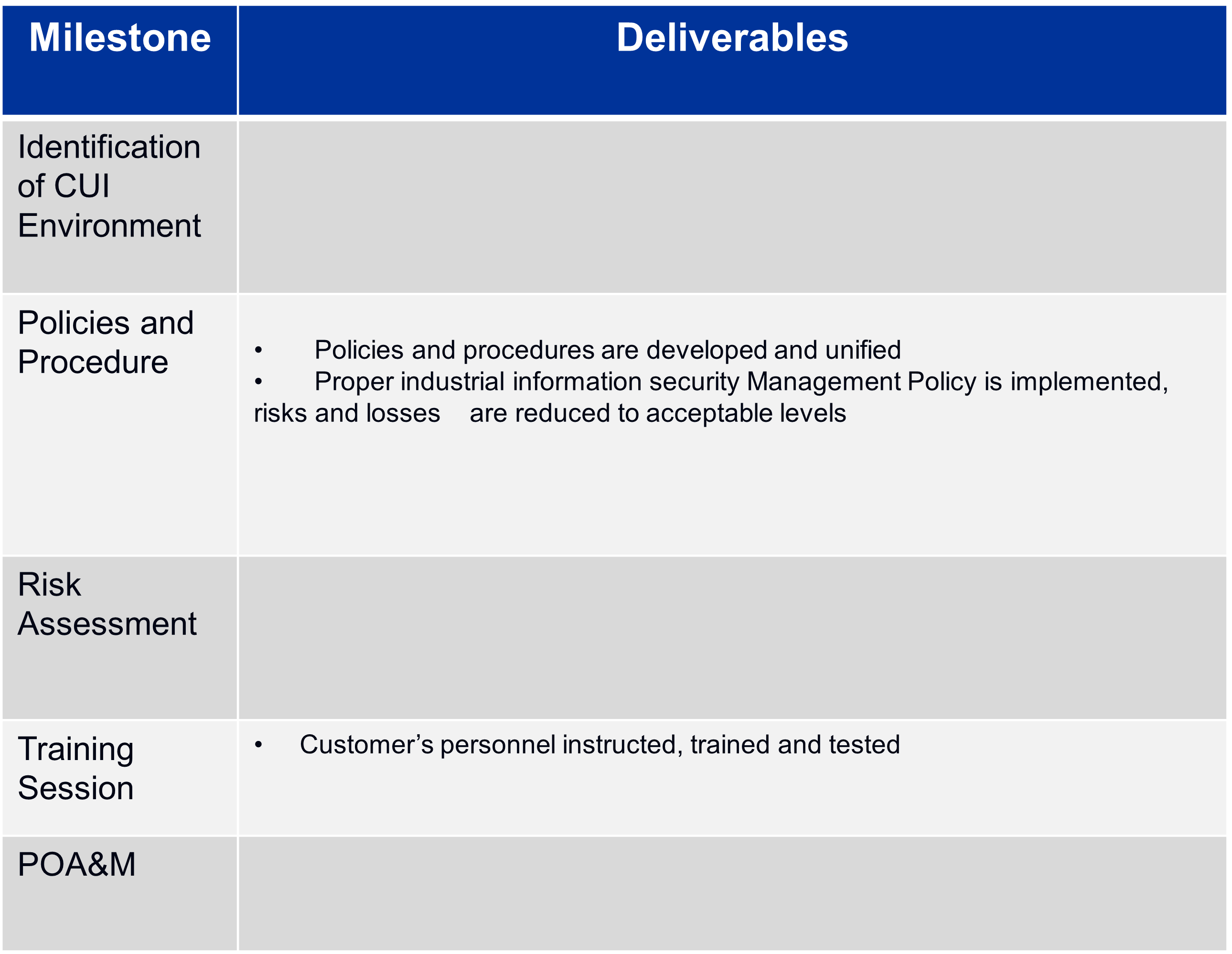
Benefits of Cyber Security Model Certification
- Creation of security documentation, including policy and procedures
- Helps in detecting & eradicating vulnerabilities, caused by flaws or are caused by poor maintenance of hardware, systems, and ICS applications
- Prevents shortfalls in production by external adversaries
To Secure SCADA System, several serious precautions should be applied such as;
- Multi-Level Security check with definite and strict roles
- Multi-Channel Security System over several channels
- AI-based authentication with unique tokens
- IP Tracking
- Proxy detection
- DOS attack suppression
- One Time Password (OTP)
- Hardware Signature Detection
- Crossover Coding avoidance
- Data Hiding
- Dynamic Hashing
- Open source dependent operating systems
- Server and Database security reinforcement
Riskpro SCADA Services
- Security audit and assessment of IT/OT infrastructure and SCADA Systems
- Hardening of industrial IT/OT systems
- Security implementation of industrial IT/OT systems
- Disaster recovery and Business Continuity Management at industrial enterprises
- Enterprise Awareness
Riskpro's Approach For Any SCADA Project
- Reviewing the complete IT infrastructure, Networking, Business Applications, Data Security, and controls
- Aligning the IS strategy to business strategy enables companies to invest in proper IS Assets
- Helping in quantifying the value of IS, particularly during acquisitions or disposals
- Measuring the performance and Improvising Information Systems
- Ensuring the technology risks are appropriately controlled, and a baseline for improvement is met
- Establishing Compliance Frameworks to meet the challenges of new IS legislations internationally
- Securing the electronic Communication Channels like email, instant messages, short messages, etc., and establishing information retention policies
- Ensuring better transparency in business operations, we assist in the implementation of quality business processes by creating a common framework abiding all the legal and regulatory aspects to ensure a safe, reliable, integrated solution for IT investment optimization
Why Riskpro?
- Riskpro assists companies with expertise and guidance in achieving continuous & harmonious security.
- We have hands-on experience with the cybersecurity standards and frameworks that are included in NIST and ISO.
- We can support an organization through implementation to certification, protection of reputation, confidential information and copyrights, ensuring business continuity & Safety, including during Cyberattacks
- Riskpro has thorough technical expertise in all relevant control areas, which helps in the completion of implementation, Preventing penalties & Facilitating Industry upgrade is a competitive advantage for our customers
For more details, please email info@riskpro.in
